Cyber Security In Focus — An Interview With Expert Author, Jason Rorie
by Matt, on 31 Mar 2020
With vast numbers of people spending most of their time at home and online, cyber criminals are rubbing their hands with glee. Hastily enacted work from home programs are shifting business activities outside their normally secure boundaries, creating untested and unanticipated security weaknesses.
User behavior isn’t business as usual either. Humans are the weak link in cyber security at the best of times. With so many distractions, new tools and processes to master, and a tidal wave of “it looks real enough to me” email flooding their inbox, people are bound to make mistakes and fall for scams.

For this edition of SPT, we spoke with Houston-based cyber security expert, Jason Rorie, author of Small Business – A Hacker’s Playground: Cyber Security. We asked him who cyber criminals most like to target, what we can do to protect ourselves and our businesses, and what impact the WFH explosion in response to COVID-19 might be having.
INTRODUCTIONS
| SP: | Hey Jason, welcome to Strategic Piece Talks! We appreciate you sharing your expert opinions with us and our audience. |
| JR: | Thank you Matt! It is a pleasure to be here with you. |
| SP: | Tell us a little about yourself and how you got involved in cyber security. |
| JR: | My start in Cyber Security started over 20 years ago, while I was serving in the US Navy. I worked with a lot of military cryptography and held a Top-Secret security clearance. After the military, I transitioned into consulting for small and medium size businesses. I help them understand and protect themselves from the ever-changing threats in today’s cyber world. |
| SP: |
Awesome. We obviously love the fact that you’re an entrepreneur and focus a lot on small businesses – not to mention making them the focus of your book. We’ll chat more about that later but first let’s dig into the meat and potatoes of today’s discussion. |
AM I A TARGET FOR CYBER CRIME?
| SP: | I think we’re all aware that cyber crime is a big deal these days. It’s not just email scammers promising to send us $20 million from a deceased Nigerian prince. What are the most common forms of cyber crime that you see and try to defend against? |
| JR: |
The most common threats are still the email scammers, but they have progressed a lot way from the Nigerian prince scams! Over 90% of information breaches start with an email, so it’s essential to educate and protect people about email phishing. In addition to worrying about the human side of hacking, you still have to stay protected against traditional hack attempts on our firewalls and other equipment. There are still bad actors out there that are trying to “kick in the front door”. |
| SP: | Like any criminal, these hackers want to prey on the weak – on people who make it easier for them. What are some of the ways we expose ourselves to an attack? |
| JR: | Absolutely — hackers like it easy. They prey on people who share too much online, those who are fooled easily, and individuals who don’t take the preventative measures to keep their data safe. |
| SP: | Can you give us some examples? |
| JR: |
The first group I call the “social butterflies”. Let’s be honest: The more you put online, the easier you are to hack. Now, we’re not saying being social on social media is a bad thing, but there are measures you should take to ensure that your private information won’t be used against you. Hackers are known to troll social media for photos, videos and other information that can help them better target you and/or your company in an attack. Many individuals’ social media accounts are public, and they regularly share personal information like their location, birthday, relationships, and place of work. Hackers are gathering this information and plotting ways to make you their next victim. Keep your firewall and anti-virus up to date, use strong passwords, and be cautious about who you accept as friends and followers online. If this has got you thinking, go ahead and search for yourself online to see what information about you is out there! |
| SP: | Interesting. Alright, so what if we’re practicing good social media distancing? Sorry – couldn’t resist that one this week! |
| JR: |
Ha-ha. Well, another at-risk group are the “macho men”. They say things like “That could NEVER happen to me!” It’s such a risky sentence, yet so widely spoken. Small and medium-sized business owners tend to think they are invincible when it comes to cyber-attacks, but this couldn’t be further from the truth. In fact, you’re at risk every single day that you refuse to upgrade your security systems. Your business might as well have a red target painted on the front because that is exactly how cyber criminals will perceive you if you have this mindset. Small and medium-sized businesses are becoming a favored target due to a lack of awareness of the threats surrounding them – or a refusal to take those threats seriously. |
| SP: | Yeah, it’s amazing how blasé some people can be, even when experts are shouting about this stuff from the rooftops. But there are some pretty amazing scams out there, right? Even smart, risk-averse people aren’t entirely safe, are they? |
| JR: |
Unfortunately, you’re right. Phishing scams are by far the top tactic that hackers use to get what they want, and people who are easily fooled are more likely to fall prey to them. Hackers are becoming experts at social engineering and carefully craft their phishing messages to fool more people than ever, even people you would not otherwise consider “gullible.” The best protection is incredibly simple: when you’re online, don’t click something unless you’re expecting it and you’re positive it’s from someone/something you recognize. Always hover over the link to see if the source is genuine and always call the sender if an email seems suspicious. Repeat after me: Think before you click! |
| SP: | Think before you click! So easy to say – why is it so hard to do? We’re always in such a hurry, I suppose. |
REMEMBER WHAT YOUR MOM TAUGHT YOU
| SP: | So, what are some other simple things we should all remember to help minimize the risks here? |
| JR: | I like to tell people that the lessons their mom taught them as a child can help them remember basic cybersecurity. |
| SP: | Ha-ha, alright, let’s see how this goes. I was raised in a foreign land, you know? |
| JR: | Well, let’s face it, no matter where you grew up, your mom was (and is) always right. Even as a stubborn teenager, you knew in the back of your head that she probably knew what she was talking about. It might have seemed irritating, but you look back today and realize your mom was a smart woman, right? |
| SP: | For sure. My mum (English spelling) will be reading this, so I’d better say yes, hadn’t I! Tell us what we’re supposed to have learned. |
| JR: |
Without some basic cybersecurity common sense, even the best technology in the world can’t keep you from falling victim to a cyber-attack. Cyber criminals want your data, identity, money and more, and, as Mom will tell you, money doesn’t grow on trees! Also, don’t give out your passwords or account information to anyone— not even to your mom! |
| SP: | Great advice. Sorry, mum, it’s for the best. What next? |
| JR: |
Do you remember her telling you not to touch something? She probably said something like: “You don’t know where that’s been”. |
| SP: | I think today’s catchphrase would be “Don’t touch that, you might pick up a virus!” |
| JR: |
You’re on a roll today, aren’t you? But yes, it’s also essential to be cautious when browsing the web, downloading files and opening links or attachments. Never download a file or attachment if it seems untrustworthy or is unexpected. Viruses are programmed to harm your computer by damaging programs, deleting files, and destroying the hard drive. Even less significant viruses can disrupt your system’s performance, deplete computer memory, and causing frequent computer crashes. Make sure you’re implementing anti-virus software and keeping it up to date. |
| SP: | Sage advice. Is there more? |
| JR: |
Oh yes, Mom had two or three more pieces of wisdom. The next one I like is that there are consequences for your actions. No kid ever wanted to hear this saying! Life was new and exciting and the last thing a teenager wanted to think about was what the consequences might be for their actions. Young companies can have a similar mentality of not wanting to think about their choices and the consequences those choices might bring. In cybersecurity, the choice to not hire a cybersecurity professional or not to pay for employee cybersecurity training can have dire and expensive consequences. Companies that choose to be prepared can respond quickly and efficiently to cyber-attacks, which can save them millions. Mom knew that life choices had consequences and in a business context we would be ahead if we thought more about the consequences for cyber risk. |
| SP: | I like it. I have two teenage kids, so I’m totally with you on that one. |
| JR: | My next favorite is to always clean up after yourself. |
| SP: | (Furtively glances around the room to assess clean-up requirements) |
| JR: |
In this case, I mean clean up your computer. When software is no longer supported, it’s not merely useless; keeping outdated software on your computer is dangerous. When companies stop releasing security patches and end support for a product, hackers jump at the opportunity to target these unpatched vulnerabilities and steal, expose, or hold data for ransom. The vulnerabilities that outdated, end-of-life software expose are low hanging fruit for cyber criminals. Go clean your computer! Uninstall anything you don’t use. |
| SP: | Wow, I hadn’t thought about that one at all. To be honest, I couldn’t even tell you what programs are installed that I don’t use any more. Making a note to myself to look into that one! Give us one more before we switch gears. |
| JR: |
Alright, let’s go with “if you don’t try, you won’t succeed.” Cybersecurity is a daunting area that can seem like a black hole. Some companies want to pretend it’s not important, so they don’t have to put the time and effort into a comprehensive response plan or an updated password policy. But if you don’t try, you will never get better at it. If you don’t attempt to tackle the hard issues, time could run out and make those issues your highest priority. By not trying at all, a company is instantly failing. Taking all the right steps to protect your business can seem daunting, especially when you tackle them on your own. So, call a professional! We will be your mom and do your dirty laundry for you! |
| SP: | Excellent. Hopefully some of our readers will reach out to you at Elevated Technologies about your laundry and IT services. It definitely makes sense to me that they’d want professional advice and support to help tackle this. |

YOU ARE THE WEAKEST LINK
| SP: | The next thing I want to ask you about is why technology isn’t just making this all go away. How come the humans are still the weakest link? |
| JR: |
That’s a great question. Cybersecurity may start with measures like a firewall, antivirus software, two-factor authentication, and spam filters, but it doesn’t stop there. Server and network security measures can only go so far. Cyber criminals don’t need to engineer a complex and technical method to gain access to your business’s infrastructure. Sometimes, all they need to do is lure a gullible or distracted employee into clicking a link or opening an attachment. Educating your staff on cybersecurity awareness is an essential component of business security. Believe it or not, employee negligence is a primary cause of data breaches and with these breaches costing an average $3.92 million, you simply must factor in the role your employees play. Cybersecurity is most effective when it’s a team effort, especially in the workplace! |
| SP: | Four million, on average? That’s definitely enough to put most of our clients out of business. When you talk about raising employee awareness, what are some of the biggest things they should remember? |
| JR: |
We focus on four ways that your employees could be putting your business at risk – although there are more, obviously. The first one is poor password management. Sometimes, a password is the only barrier between a cyber criminal and your business information. What if that barrier could be easily broken into or broken down? There are several programs that attackers use to guess or crack passwords. If your employees aren’t implementing the best practices for password management, your business could be in danger. Actions such as updating passwords every month, using different passwords for different logins, and including a combination of characters in your password are just a few security measures you can enforce today. Make sure your employees are taking password security seriously. |
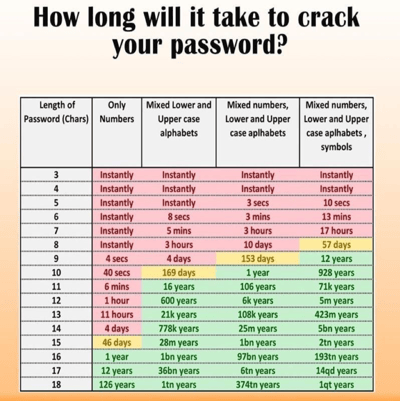
| SP: | So true. I saw an infographic recently about how quickly a criminal can crack your password relative to its length and complexity. It’s pretty eye-opening.
What’s your second area for employee training? |
| JR: |
The next one is a failure to recognize spear-phishing. That’s when a cyber criminal sends fraudulent emails that appear to be from a trusted sender in order to trick targeted individuals into revealing confidential information or performing an action that seems legitimate. Spear phishing is usually extremely successful because the scammers spend a lot of time researching their target and specially crafting the email they send to them, making it more believable. Being able to identify these phishing emails is the first line of defense. It’s essential to provide employee training on what to look for because cyber criminals can easily make them look extremely legit. our readers should take a look at Hook Security’s Blog that lays out different aspects of a phishing email to be wary of. |
| SP: | Awesome, we’ll include that link in the post, thank you. |
| JR: |
My next recommendation is to talk with your staff about being overly social on social media. As we already discussed, cyber criminals do their research. They social engineer their target before an attack to better craft the information they send them. In today’s day and age, social media is a popular tool that attackers use to gather information about their potential victim. Small details that employees post online – like names of their pets or important personal dates – can be a big hint for cyber criminals, leading to a cracked password. Now, we’re not saying that your employees should immediately cancel their social media accounts, but it is necessary to talk about oversharing on social media and consider implementing a social media policy. Keeping accounts private, being wary about friend/follow requests, avoiding oversharing, and not mentioning the name of your company are just a few ways your employees can do their part in protecting your business online. |
| SP: | More social media distancing! I’m surprised no one has trademarked that yet. Probably they have. Want to give us one more tip here? |
| JR: |
Alright, let’s talk about compromising sensitive information. Most of the time it’s accidental, but employees create cybersecurity risks by giving unauthorized individuals access to sensitive information. Scenarios like walking away from an unlocked computer/device and/or leaving passwords written down where they can easily be found pose a huge threat not only to the company but to themselves. Employees at businesses that store private client information – like credit card numbers, bank information, social security numbers, or account passwords – must be extremely vigilant in protecting it.Companies should develop strict security policies and communicate them to their employees to keep this sensitive information secure. It’s not just about weak passwords or gullible employees. You need to act holistically when it comes to protecting your business infrastructure, devices and data. |
| SP: | And you guys can provide cyber training as well as monitoring services, correct? |
| JR: | Absolutely. Elevated Tech can secure and monitor your systems to diagnose and patch vulnerabilities before they become a threat, but we will also provide cybersecurity training to you and your employees to better protect your business. |

AND TO MAKE MATTERS WORSE…
| SP: | Before we wrap, I’d like to hear your thoughts on what the current situation is doing to cybersecurity. We’re in uncharted territory with millions of people who normally work at an office or other kind of business location being forced to stay home and work online. Same thing for our kids whose schools and colleges are throwing up virtual classrooms while they can’t teach in the classroom. How do you see that affecting cybersecurity? It sounds like the cyber criminals should be having a field day. |
| JR: |
They are having a field day. They understand as well as anyone what is happening. They know businesses are sending people instructions on how to use unsecured equipment to access their company’s network. This gives the hacker’s a huge playing field for malware, viruses and more social engineering. People need to stay vigilant when using their home computers while connecting to their company’s network. Business owners, if possible, need to be sending staff home with corporate systems that are monitored, managed, and secured by their IT staff. I understand the panic and the need to move quickly right now, but you cannot afford to sacrifice your security. |
| SP: | Interesting stuff, Jason. We appreciate your perspectives. Hopefully things will calm down a lot in the coming weeks and months. |
CLOSING THOUGHTS
| SP: | It’s been a pleasure chatting with you. We mentioned in the intro that you’re a published author these days. Can you tell us a bit about why you decided to write the book and what that process was like for you? |
| JR: |
Sure, thank you. I appreciate the plug! The book is called Small Business – A Hacker’s Playground: Cyber Security and I wrote it for small business owners. My goal is to get small business owners out of the mindset that cyber threats are too big for their business. These owners think that a cyber incident will never happen to them because their business is “too small.” This is never the right mindset to keep because an attack CAN and WILL happen to you if you don’t have the proper cyber security in place. You have to put protection methods in place to keep your business safe in today’s cyber world. Writing the book was a lot of fun! I’m able to use it as a platform to help the community that I love and am passionate about — small businesses. I wanted to make the book relatable and understandable for anyone that picks it up. I didn’t want to bore anyone with “geek speak”! I wanted to raise awareness about the real threats that are out there. And I think the book accomplishes that goal. |
| SP: |
Well, I commend you on the effort and the product! We’ll post a link to the book in our blog post and encourage anyone who wants to learn more about the topics we’ve skimmed through in this conversation to buy it and read it. Thank you, Jason! Enjoyed the chat and look forward to having you contribute to more Strategic Piece Talks down the road. |
Here’s how to connect with Jason and Elevated Tech:
Facebook | LinkedIn | Instagram | Vimeo
Photo Credits
Photo by Kristina Flour on Unsplash
Photo by Jake Noren on Unsplash
Photo by Steinar Engeland on Unsplash